In an era where data is as valuable as currency, attackers are constantly on the hunt to fill their pockets with data and cash. This exploration into the use of open-source intelligence (OSINT) to uncover personal and organizational information illustrates not just the ease with which this can be done, but also the potential consequences.
The Power of OSINT
Open-source intelligence (OSINT) refers to the collection of information from publicly available sources to be used in an intelligence context. In the digital age, the amount of data available at our fingertips is vast—from public records and social media to professional websites like LinkedIn and data leaks.
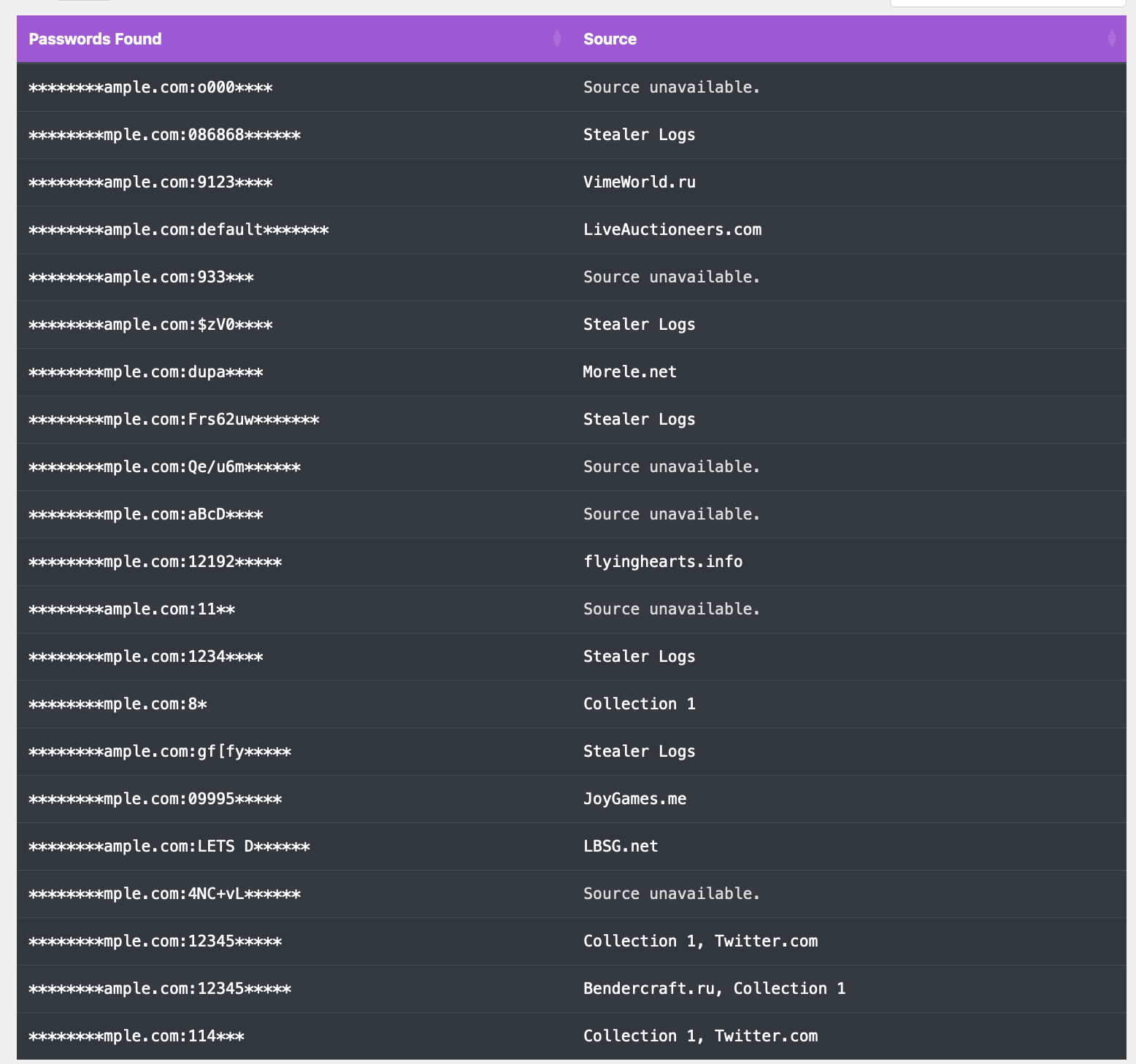
To understand the power of OSINT, I conducted an experiment targeting a tech company, focusing on its two co-founders—the CEO and the CTO. I was able to uncover not just personal emails and addresses but also passwords that had been leaked in various database hacks. Tracking where these personal emails were registered, I could even deduce the IP addresses of the founders.
For example, you can search domains with online tools and find all associated passwords that have leaked.
When I examined the company’s presence online, I discovered a consistent email format used across the organization (firstName.lastName@company.com).
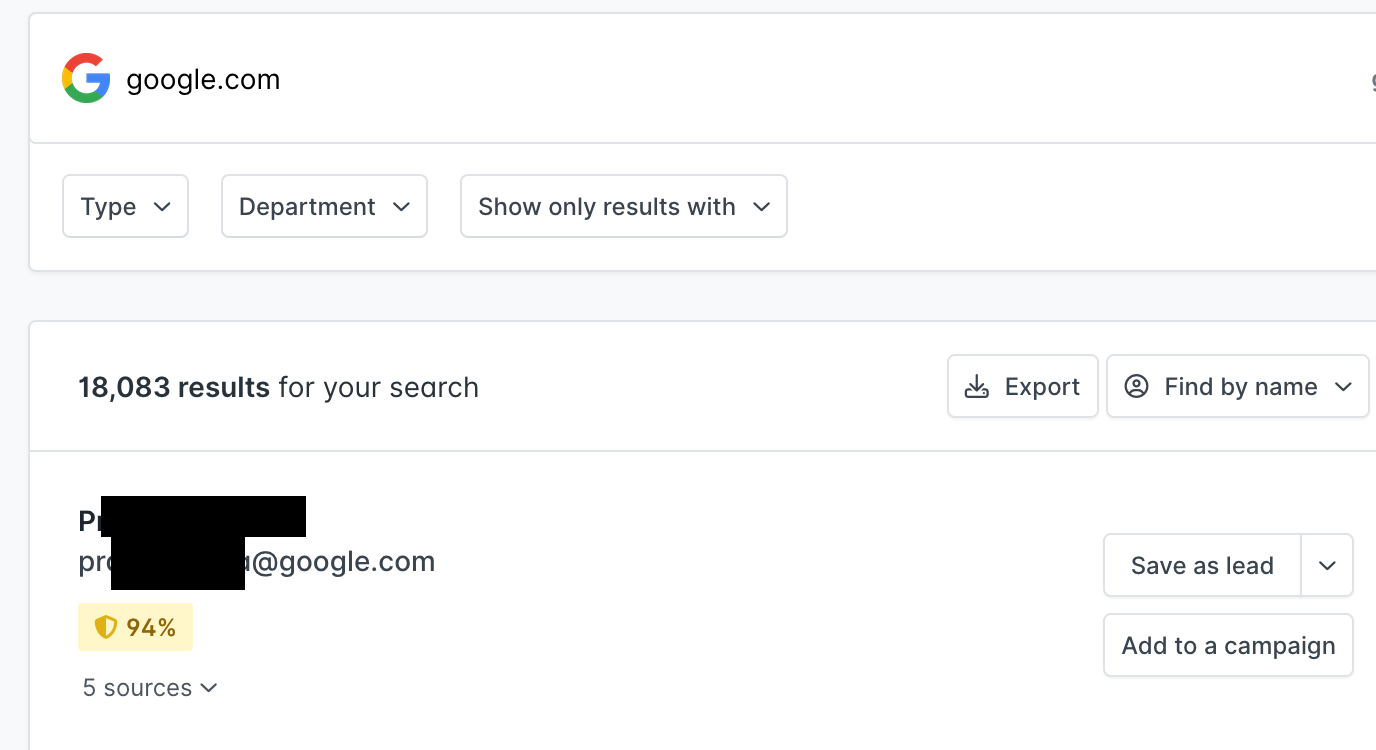
Leveraging LinkedIn, I compiled a list of hundreds of employees. With their names and the company’s email format, it was simple to construct potential email addresses, creating a wide vector for a potential phishing campaign. Attackers can use this to gain a foothold within the organization and exfiltrate private company information.
The Risks Revealed
The gathered data can be misused in several ways:
- Phishing Attacks: By creating emails that look like they come from a trusted source, attackers can trick employees into giving away sensitive information or downloading malware.
- Identity Theft: With enough personal information, an attacker could attempt to steal someone’s identity, business or personal accounts, impersonate them, and more.
- Business Email Compromise (BEC): Attackers could impersonate senior executives to authorize fraudulent transactions.
Protecting Against OSINT Threats
Educate Your Team: Continuous training is essential. Employees should be aware of the dangers of phishing and taught the importance of maintaining strict privacy settings online. Encouraging the use of unique passwords for different sites can prevent attackers from using a leaked password from one site to access another.
Implement Strong Security Measures: Adopt multi-factor authentication to add an extra layer of security beyond just passwords. Encrypt sensitive data to make it harder for unauthorized users to view it if they gain access. Regular security audits help identify and rectify vulnerabilities before they can be exploited.
Monitor and React: Utilize services that monitor the web for leaked information and alert you when your organizational data is compromised, such as UpGuard BreachSight or BitSight. Keeping an eye on unusual network activity and having an effective response plan are crucial to quickly mitigating damage and restoring operations.

Conclusion
This exploration into OSINT underscores a vital lesson: while information can empower us, in the wrong hands, it can also expose us to significant risks. Recognizing these dangers is the first step toward defending against them. Armed with knowledge and the right tools, organizations can protect not only their data but also their financial and personal security.


