When we think about physical security, the image that often springs to mind is a padlock, symbolizing safety and security. But just how secure is it? A skilled attacker might use a lock pick set and open the lock within minutes, but what about the average person? Could they gain access just as easily?
Let's examine two locks. Which one would you say is more secure?

The one on the left certainly appears formidable. With a weight of over 3 pounds, it would undoubtedly take a while to cut through. But would you believe that both locks could be opened in less than 5 seconds using simple bypass techniques?
First, let's consider our smaller Master lock.
Impressive, isn't it? Now, let's move on to the larger lock.
Surprisingly, it's just as easy to open as the first. So, what's the secret?
The first tool we use is a comb pick.

A comb pick, or comb bypass, is a tool designed to defeat certain types of padlocks, like our Master Lock. The tool is named for its resemblance to a hair comb, with "teeth" of varying lengths. Here's a basic rundown of how it works:
The comb pick is inserted into the lock's keyway. The teeth of the comb are designed to push both the key pins and driver pins in the lock's pin stacks completely above the shear line, which is the point at which the inner cylinder of the lock can turn freely.
Normally, the key lifts the key pins, and the driver pins stay at the shear line, allowing the lock to turn. However, the comb pick lifts both sets of pins above the shear line, effectively bypassing the lock's pin tumbler mechanism, which usually prevents the lock from opening without the correct key.
With all the pins lifted above the shear line, the comb pick can then turn the cylinder as if it were the correct key, opening the lock.
For our second lock, we employ a bypass driver.

A bypass driver is used to open a lock without manipulating the lock's actual pin tumbler mechanism. This method is often faster and less likely to damage the lock than traditional lock picking.
The Bypass Driver is specifically designed for certain models of American (brand) padlocks and padlocks that have cloned the American design. These locks have a specific vulnerability that allows the bypass driver to act directly on the locking mechanism, bypassing the pins entirely.
Here's a brief overview of how it works:
The bypass tool is inserted into the lock's keyway. The tool is maneuvered past the pin tumblers, which are the parts of the lock that would normally need to be set in the correct position by a key.Once past the pin tumblers, the tool interacts directly with the lock's actuator, which is the part of the lock that actually moves when the correct key is inserted. By manipulating the actuator, the lock can be opened without needing to pick the pins or use a key.
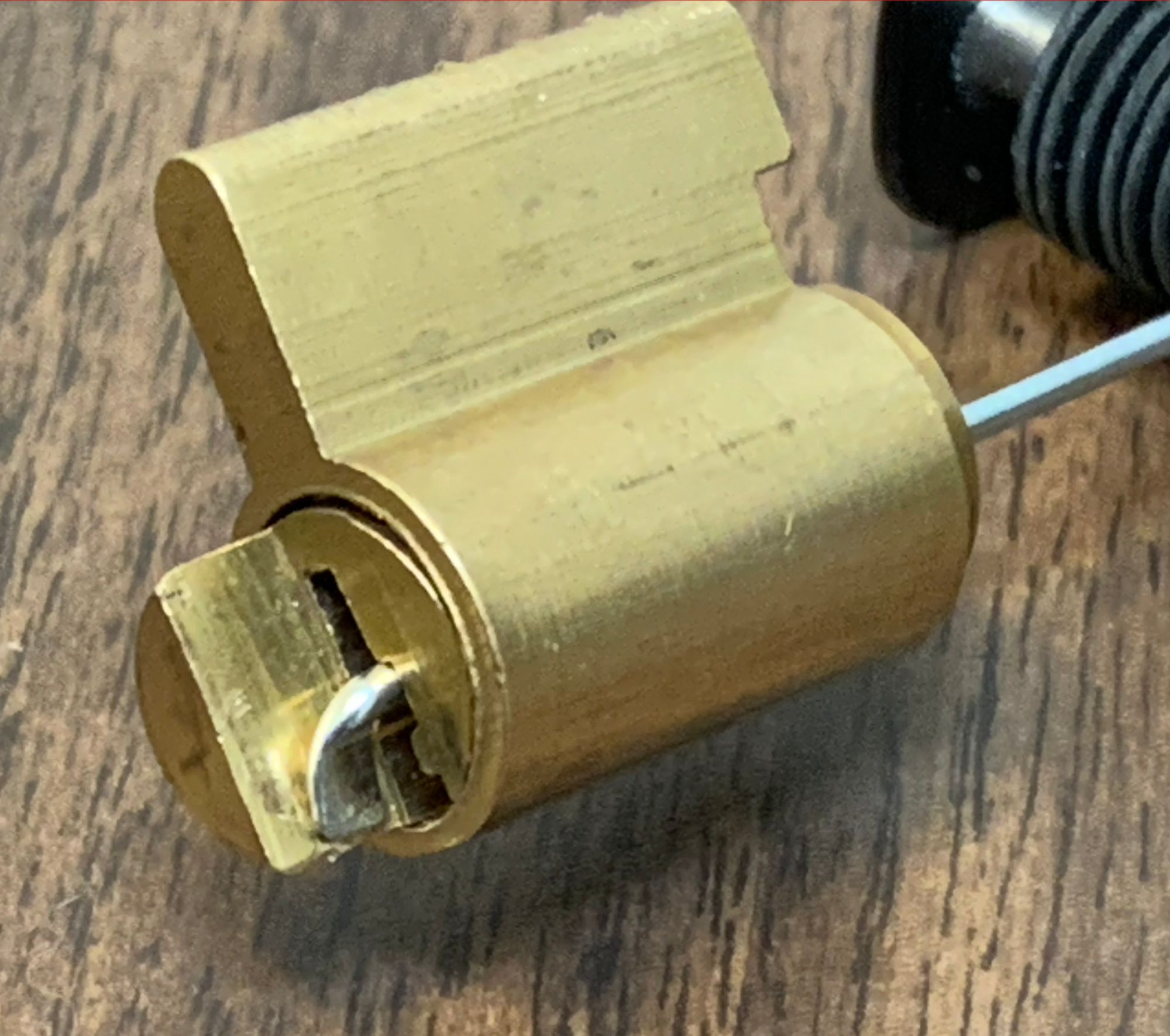
In conclusion, the physical security provided by padlocks may not be as robust as we often perceive. While they serve as a deterrent to the average person, they can be easily bypassed by those with the right knowledge and tools. The comb pick and bypass driver are just two examples of tools that can exploit the vulnerabilities of certain locks, opening them in mere seconds.
This highlights the importance of understanding the limitations of our security measures. While padlocks can provide a level of security, they are not infallible. Not all padlocks are created equal and cost does not always correlate to quality. It is important to assess what you are protecting and research what best fits your needs. Personally, we spend a lot of time watching videos from the Lockpicking Lawyer for known bypasses and general reviews of locks. It's crucial to complement physical security measures with other forms of protection, such as surveillance systems or alarm systems, to ensure a comprehensive security strategy.
Remember, the goal of security is not to create an impenetrable fortress, but to make unauthorized access as difficult as possible, deterring potential intruders. Stay informed, stay vigilant, and always strive to improve your security measures.


